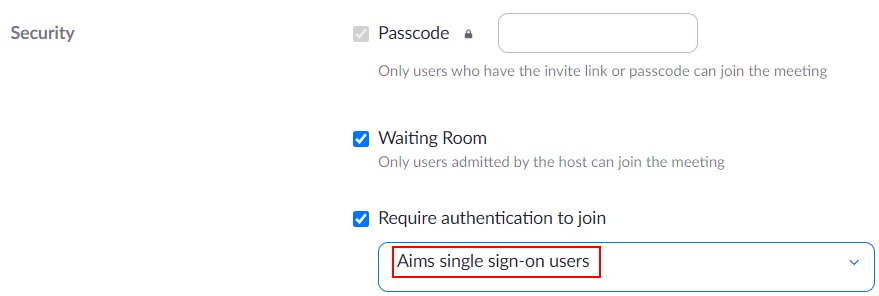
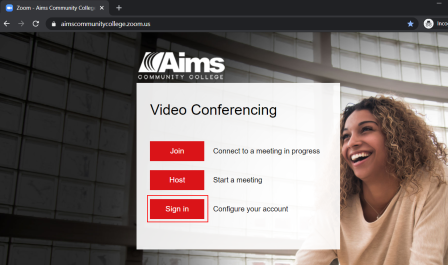
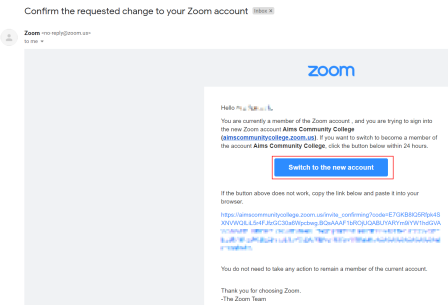
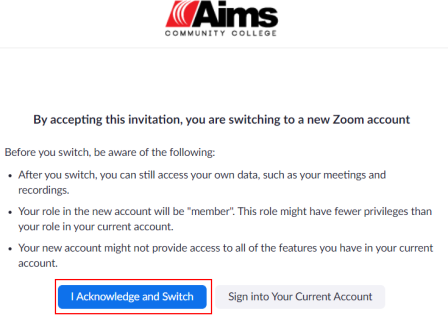
In order to keep your Zoom meetings secure and free of uninvited people, never post the meeting link, meeting ID or passcode publicly such as to a website that does not require authentication or on social media. Meeting information should be shared through authenticated means only such as Aims email or the D2L portal.
“Zoombombing” is the term for when individuals “gate-crash” Zoom meetings. These uninvited guests share their screens or video feed to disturb real attendees with bothersome material including pornographic or violent content. These acts are often perpetrated via Zoom links that have been made public.
Public Meeting Disclaimer: Public Zoom meetings are highly discouraged because the risk of Zoombombing is significantly higher. If you must make your meeting public, please require registration and manually approve the registrants to ensure each participant is thoroughly screened. It is the meeting organizer’s responsibility to ensure that their meeting is adequately configured to avoid misuse.
We recommend using Zoom Webinar for public events as they offer a more controlled environment. Please see the “Large Meetings & Public Events” heading above for more information.
Important:
Do not record meetings that involve confidential data or FERPA protected information as this data is not approved to be stored in the Zoom cloud service. Consult Aims Information Security if you have a need to record this type of meeting.
Report Zoombombing
While Zoombombing disruptions often take the form of profanity, hate speech, or pornography, they have also been known to include threats. If you receive threats during a Zoom meeting, please notify Aims Campus Safety & Security immediately.
If you are the victim of Zoombombing, please report it by emailing the Aims Information Technology department.
Please include the following information:
- The date and time of the incident
- The meeting ID of the session that was interrupted
- A summary of what happened
- What action was taken (e.g., was the meeting halted, or was the intruder removed)
- Indicate whether or not the session was recorded. If it was, please retain the recording if needed for an investigation.
We encourage you to take steps in advance of a session to make it harder for uninvited guests to break into your session, using the recommendations outlined above. You can also utilize the following Zoom security resources:
Best Practices for Securing Your Zoom Meetings - a walk-through guide on the various security settings for virtual meetings.
Best Practices for Securing Your Virtual Classroom - This excellent Zoom blog gives advice for those using Zoom for remote teaching.